Exploiting Continuous Integration and Automated Build Systems Defcon 25
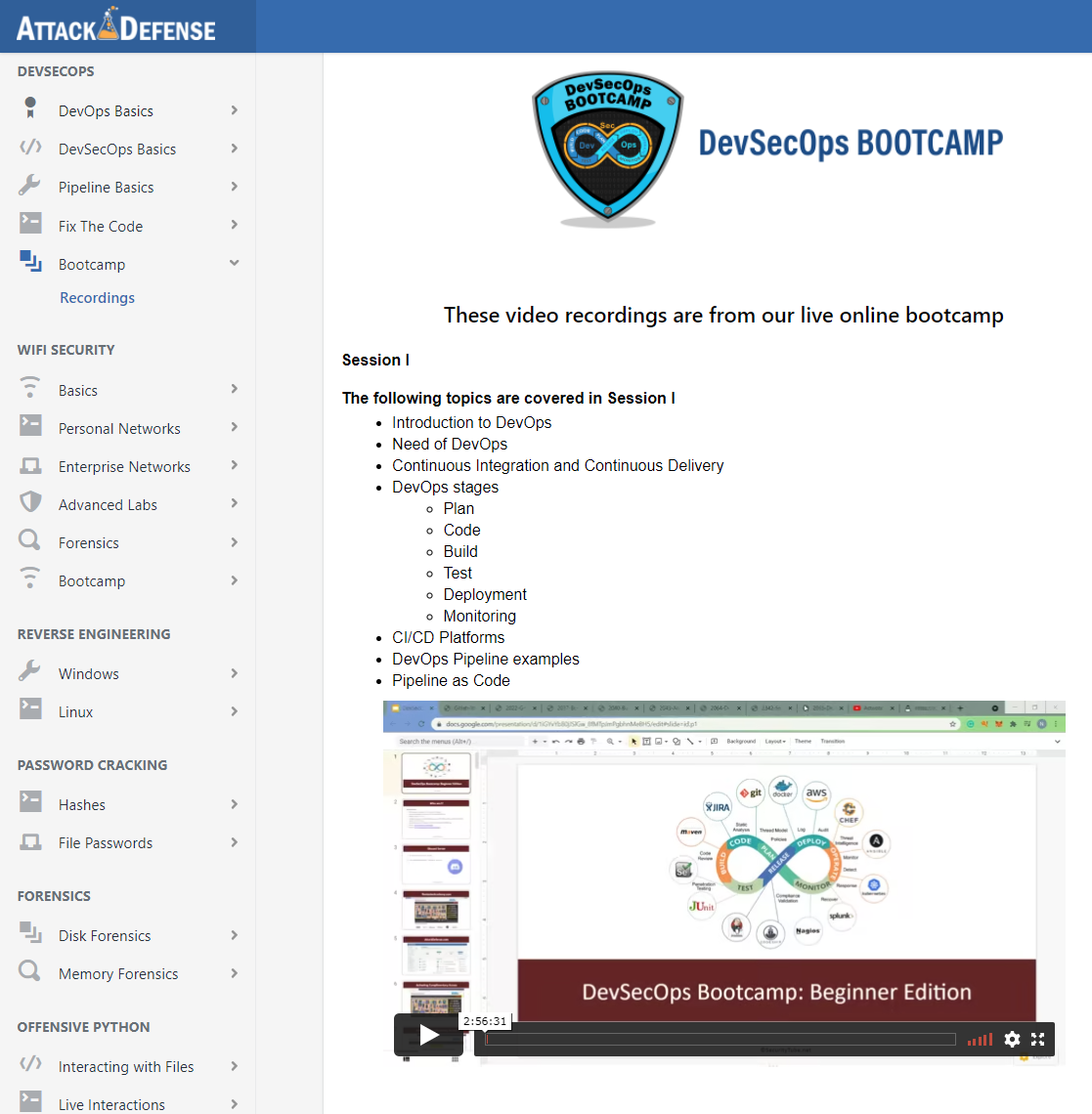
On-Demand: DevSecOps: Beginner Edition Bootcamp
Get a hands-on introduction to DevSecOps basics with a focus on implementing Devops and DevSecOps pipelines in on-premise, hybrid and on-public cloud models.
Recordings of this bootcamp are now available as part of our annual subscription. Subscribe to enjoy:
- Access to all on-demand bootcamps and relevant labs, including this one
- 2200+ hands-on labs covering another 130+ subtopics
Write your awesome label here.
Upon logging in to the AttackDefense lab platform, annual subscribers will be able to access recordings of all our on-demand bootcamps and associated labs.
Prerequisites
1. Basic knowledge of computers and networking
2. Familiarity with the Linux Operating System
3. Familiarity with DevOps components is useful, but not essential
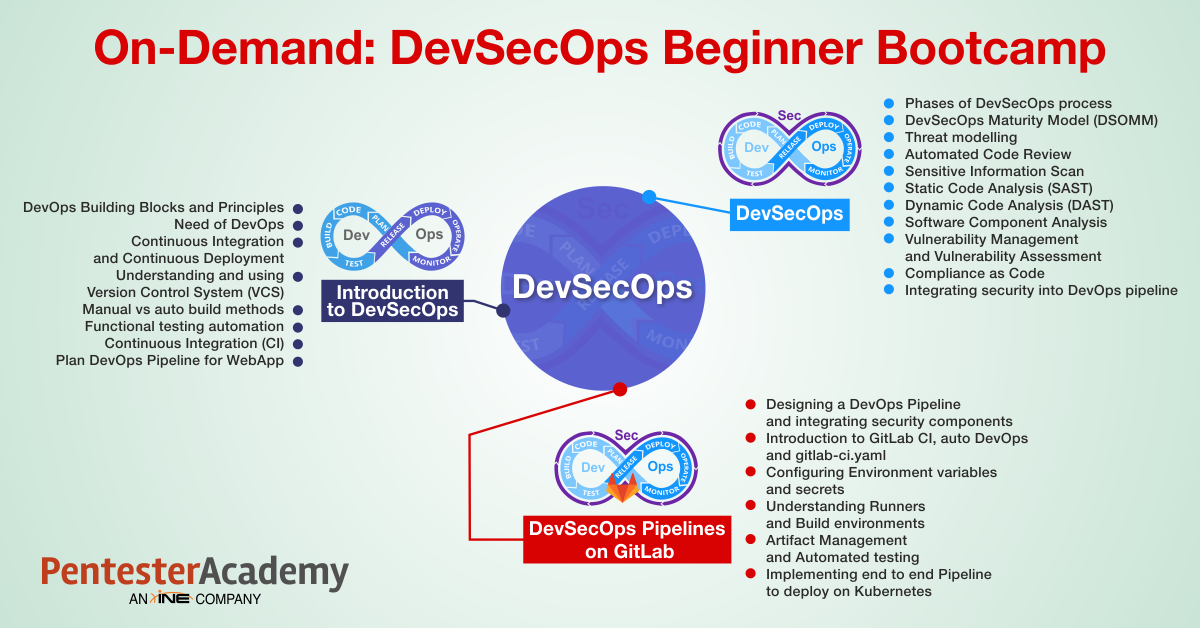
Module I: Introduction to DevOps
-
What is SDLC?
-
What is DevOps?
-
DevOps Building Blocks and Principles
-
Need of DevOps
-
What is Continuous Integration and Continuous Deployment?
-
Continuous Integration to Continuous Deployment to Continuous Delivery
-
Continuous Delivery vs Continuous Deployment
-
General workflow of CI/CD pipeline
-
Phases of DevOps Pipeline
-
Code Environment (IDE)
-
Version Control System (VCS)
-
Basics of Git VCS
-
Self Hosted VCS i.e. Gitlab, SCM
-
Publicly available VCS e.g. GitLab, GitHub, BitBucket
-
Building the Project
-
Manual Build vs Automated Build
-
Build Systems e.g. Maven, make, Dockerfile, Packer
-
Testing
-
Manual Testing vs Automated Testing
-
Automated Unit Testing e.g. JUnit, Pytest
-
Automated Functional Testing e.g. Selenium
-
Deployment
-
Manually creating the setup
-
Infrastructure as Code e.g. Ansible, Chef
-
Continuous Integration (CI)
-
Benefits of CI
-
CI solutions e.g. Jenkins, GitLab CI
-
Lab: Continuous Integration lab for Django Webapp
-
Monitoring
-
Importance of Monitoring
-
Monitoring with NagiOS
-
Concept and explanation what to monitor
-
Maintenance
-
Issue Tracking
-
Documentation
-
Case studies on DevOps Pipelines
-
Plan a DevOps Pipeline for a WebApp
-
Implement DevOps Pipeline for an on-premise model
Module II: DevSecOps: Adding Security to DevOps
-
What is Secure SDLC?
-
Secure SDLC phases
-
DevSecOps Maturity Model (DSOMM)
-
Adding Security to DevOps
-
Phases of DevSecOps Pipeline
-
Threat modelling
-
What is Threat Modelling?
-
STRIDE vs DREAD approaches
-
Using ThreatSpec and BDD Security
-
Automated Code Review
-
What is Automated Code Review?
-
Using FindSecBugs, PMD, DevSkim tools
-
Sensitive Information Scan
-
What is Sensitive Information Scan?
-
Using Talisman, GitSecret, Trufflehog
-
Static Code Analysis (SAST)
-
What is SAST?
-
Using SonarQube, Graudit and Flawfinder
-
Dynamic Code Analysis (DAST)
-
What is DAST?
-
Using OWASP Zap, Arachini
-
Software Component Analysis
-
What is Software Component Analysis?
-
Using OWASP dependency check, Retire.js and Safety
-
Vulnerability Management and Vulnerability Assessment
-
What is Vulnerability Management and Vulnerability Assessment?
-
Using ArcherySec, DefectDojo, OpenVAS
-
Compliance as Code
-
What is Compliance as Code?
-
Using Inspec and Serverspec
-
Secret Management
-
Need for Secret Management
-
Using Hashicorp Vault, Torus
-
Case studies on DevSecOps Pipelines
-
Identify security components for the WebApp DevOps pipeline created in last session
-
Integrate the security components to form a DevSecOps pipeline
Module III: DevSecOps Pipelines on GitLab
-
Designing a DevOps Pipeline for a Django Web Application
-
Identifying the DevSecOps components to integrate
-
Introduction to GitLab CI
-
Writing gitlab-ci.yaml
-
Configuring Environment variables
-
Using secrets securely
-
Configuring Runners
-
Implementing Pipeline using GitLab CI
-
Integrating security tools
Nishant Sharma
Nishant Sharma leads R&D at Pentester Academy and Attack Defense. He has 8+ years of experience in the information security field including 6+ years in WiFi security research and development. He has presented research and conducted workshops at Blackhat USA/Asia, DEF CON China, HITB, RootCon, Packet Hacking Village, Wireless Village, IoT village and Demo labs (DEFCON USA).
Nishant's Twitter handle is also @wifisecguy, which should tell you all you need to know about his research interests.
Nishant Sharma - Instructor
Can't attend this bootcamp? Get informed about future bootcamps!
Source: https://bootcamps.pentesteracademy.com/course/devsecops-on-demand






0 Response to "Exploiting Continuous Integration and Automated Build Systems Defcon 25"
إرسال تعليق